Combining IT Technology
Cybersecurity with AI


IT Security Risk Penetration Testing
For stronger security and more peace of mind
AI Consulting &
AI Implementation
For stronger security and more peace of mind
IT Security Full Stack
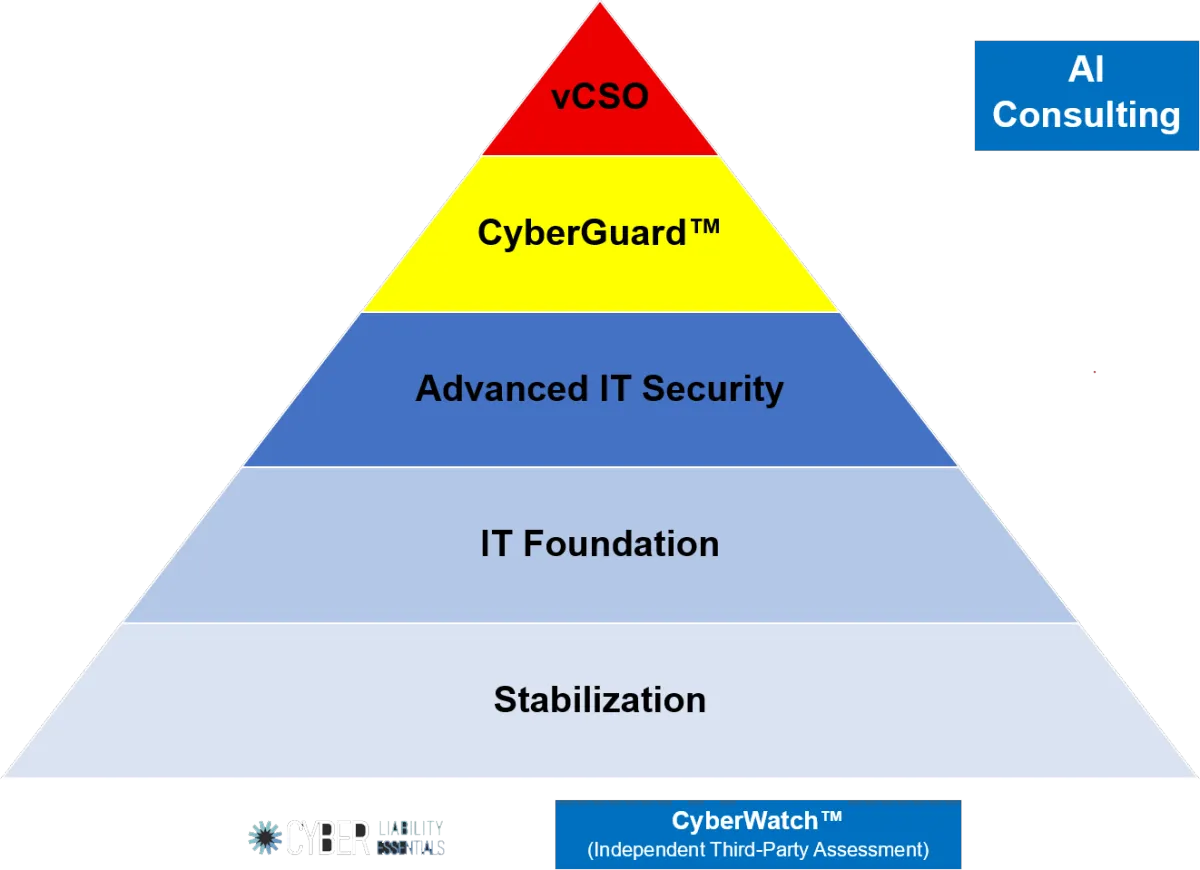

About Our IT Risk Penetration Testing Services
In a world filled with crippling cyberattacks and sophisticated hackers, your success depends on
SOLID CYBERSECURITY!
Our IT Security Services
Transforming Businesses Through Strategic Technology Solutions

IT Strategy and Planning
We work closely with your business to develop comprehensive IT strategies aligned with your goals. Our experts help you leverage the right technologies to enhance productivity, efficiency, and profitability.


Network and Infrastructure Solutions
From designing and implementing robust networks to managing cloud infrastructure, we ensure your IT infrastructure is secure, scalable, and optimized for seamless operations.

Cybersecurity and Data Protection
Safeguard your business against cyber threats with our proactive cybersecurity solutions. We implement robust security measures, conduct vulnerability assessments, and provide data backup and recovery services to protect your critical assets



IT Support and Maintenance
Our responsive IT support team is available to address your technical issues promptly. We provide proactive monitoring, system updates, troubleshooting, and regular maintenance to ensure your IT environment runs smoothly.
Frequently Asked Questions
What is an IT Security Risk Penetraion Test?
A penetration test is a unique risk assessment service that discovers vulnerabilities in your organization's environment—so you and your cybersecurity solutions provider can find and fix them before the hackers do.

How can an IT Security Risk Penetration Test benefit my business?
Here are the Top 5 Benefits:
1. Identify Vulnerabilities Before Attackers Do.
2. Improve Your Business’s Cyber Resilience.
3. Ensure Regulatory Compliance (Cyber-Liability Policies).
4. Protect Your Reputation.
5. Cost-Effective Risk Management.

What will this test do for us?
Our IT Security Pen Test gives you actionable insight into your current security and compliance risks.

What does the IT Security Risk Penetration Test test?
Your cyber defenses against phishing, insider threats, and supply-chain attacks
Inspects internal vulnerabilities and assesses the effectiveness of your cyber defense tools, system configurations, and technical security controls
Inspects external vulnerabilities that identify your organization's potential attack surf ace and scores the risks associated with any discovered vulnerabilities
Asset-specific assessments for Microsoft 365, Active Directory, and other commonly deployed IT systems

What types of businesses do you work with?
Large, Medium and Small Businesses
Industries like:
Legal
Healthcare
Architect & Engineering
CPA & Finance
Construction - General Contractors

What is the process for engaging your IT services?
Schedule a Discovery Call with one of our Risk Assessors to see if you qualify for one of our IT Security Risk Penetration Tests

Hear what our clients have to say about us


Janette DeGrazio

I've always had an excellent experience working with Eric and his team! They are extremely professional and reliable. I highly recommend Elliptic Systems!


James Whichello

Elliptic Systems reviewed both my personal and professional networks' resilience against hacking and fraud. They introduced novel solutions that give me confidence in my cybersecurity as we emerge from the pandemic to ever increasing threats from scammers. Eric's knowledge, service, attention to detail and after sales support is second to none!


Todd Cummings

Eric and his staff are quick to respond and up-to-date on current IT issues. I appreciate all the help they have given me.
Office: Seattle, WA
Office: Phoenix, AZ
Office: Hawaii
Call 425-441-9500
Call 480-207-7979
Call 808-883-3222
Email: [email protected]
Site: www.ellipticsystems.com
